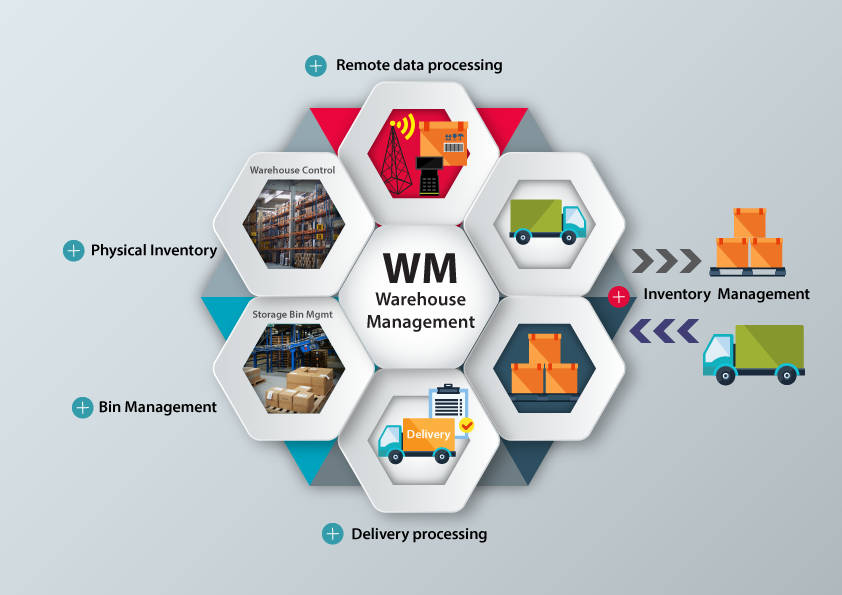
UEM Software (Unified Endpoint Management) allows businesses to monitor company data, licenses, applications, usage, and security across a wide range of devices from a central location. Endpoint management software, mobile application management (MAM) software, mobile device management (MDM) software, patch management software, and other endpoint-focused management solutions are all part of UEM. Endpoints covered by modern UEM technologies include (but are not limited to) computers, mobile phones, tablets, wearables, and IoT devices.
Table of Contents
Why is UEM Software Useful?

UEM Software is mostly used by internal IT and security teams. These tools provide a more comprehensive view of all devices used for business purposes at an organization, including company-owned and BYOD (bring your own device) devices. Businesses can use UEM features to ensure that device licenses, apps, software, and data are all properly secured. The usage data provided by UEM software is also useful in determining how frequently and intensively employees use their devices.
A product must meet the following criteria to be considered for the Unified Endpoint Management (UEM) category:
- Manage a variety of endpoint types, including PC, IoT, and wearables, in addition to mobile-only endpoints.
- Configure devices for use with business-critical applications, WiFi, VPN, and other services.
- Ensure that staff devices are compliant with company rules and laws.
- Protect your employees, your company, and your data from cyber-attacks.
Top 8 UEM Software:
ManageEngine Desktop Central
Desktop Central is a unified endpoint management (UEM) solution that allows administrators to manage servers, laptops, desktops, smartphones, and tablets all from one place. It’s a cutting-edge approach to desktop management that can be scaled to meet the demands of any enterprise.
Desktop Central is a desktop management solution that adds complexity and personalization to a typical desktop management service. Installing patches, deploying software, imaging, and deploying the operating system are all normal endpoint management tasks that may be automated. It also allows you to manage assets and software licensing, as well as track software usage statistics, manage USB device utilization, and control remote desktops. Desktop Central is a desktop manager that works with Windows, Mac OS X, and Linux. Manage your mobile devices by deploying profiles and policies, as well as configuring them for Wifi, VPN, and email accounts, among other things.
Ivanti Unified Endpoint Manager
Endpoint security and management have never been more important for both IT professionals and employees as more companies move to hybrid work environments. Have peace of mind knowing that you can manage your modern device fleet in the Anywhere Workplace with Ivanti Unified Endpoint Manager.
Ivanti Unified Endpoint Manager can help with: 1) boosting user and IT productivity, 2) empowering IT Administrators to automate device and software deployment provisioning, 3) swiftly resolving user issues, and 4) fast discovering devices and software assets. Use fewer resources to get more done faster. With Ivanti Endpoint Manager, a single individual can now manage hundreds or even thousands of people and their devices.mYou can examine systems, rectify problems, and reduce desk-side visits via remote control.
Users and their profiles can simply migrate between machines, and logon times are quick. No coding or BI expertise is required to combine business and IT data into beautiful dashboards.
Microsoft Intune
Microsoft Intune is cloud-based mobile device management (MDM) and mobile application management service (MAM). You have complete control over how your company’s devices, such as mobile phones, tablets, and laptops, are used. To control applications, you can also set up custom policies. You can, for example, block emails from being sent to persons outside your company. People in your business can also use their personal devices for education or work using Intune. Intune helps ensure that your organization’s data is protected on personal devices by isolating organization data from personal data.
You can do the following with Intune:
- Choose between being completely cloud-based with Intune or being managed jointly by Configuration Manager and Intune.
- To gain access to data and networks, create rules and modify settings on personal and corporate devices.
- Apps can be deployed and authenticated on both on-premises and mobile devices.
- Control how people access and share information to protect your company’s data.
- Make sure your devices and apps meet your security needs.
Citrix Endpoint Management
Citrix Endpoint Management is a mobile device management (MDM) and mobile application management (MAM) solution for managing endpoints. Endpoint Management allows you to manage device and app policies as well as distribute programs to users. Identity, devices, apps, data, and networks are all secured to keep your corporate information safe.
Citrix Endpoint Management (CEM) is a service that allows businesses to securely deliver corporate email, apps, content, tools, and network access to mobile and tablet devices.
CEM allows you to access your company’s email, calendar, contacts, and other business apps while also protecting the company from security threats like physical loss, insecure Wi-Fi networks (such as those found in coffee shops or trains), and harmful app downloads. It also allows IT to define policies that govern the use of mobile devices and applications, allowing us to fulfill security and regulatory requirements.
Workspace ONE
Workspace ONE UEM is a single solution for managing desktops, mobile devices, rugged devices, wearables, and IoT devices over the air. With an intelligence-driven, cloud-first UEM, you can save money, increase productivity, and provide a better employee experience. At every level, deliver unsurpassed levels of process automation, unrivaled device and application control, and enterprise-level security.
To support all of your mobility use cases, manage the whole lifecycle of any endpoint — mobile (Android, iOS), desktop (Windows 10, macOS, Chrome OS), rugged, and even IoT – in ONE administration console. Combining a self-service unified app catalog with SSO, Assist remote assistance, and Privacy Guard to secure user data, deliver a wonderful employee experience that is uniform on every device, no matter where employees work. Use cognitive insights and rule-based automation to improve employee satisfaction, reduce IT workload, and allow proactive management and security. Get a sense of what’s going on and what’s important. Conditional access and compliance standards help protect data and defend against modern security threats. Workspace ONE UEM provides a comprehensive security solution that includes user, endpoint, app, data, and network protection.
IBM MaaS360
IBM Security MaaS360 with Watson is a unified endpoint management (UEM) system that revolutionizes how businesses support people, apps, content, and data across all devices. Its open, cloud-based platform interacts with popular security and productivity applications, providing immediate value to modern corporate leaders.
1) Comprehensive AI: MaaS360 is the only UEM platform that uses AI to provide administrators and end-users with contextually relevant security insights.
2) Best-in-class SaaS: Reduce time-to-value with an open platform that allows for comprehensive integrations with your existing infrastructure and major technology vendors’ apps.
3) Detection and response to threats: At least one of your devices is infected or hacked right now. Detect and automate remediation across your entire network, including apps and devices.
IBM provides a wide range of technology and consulting services, as well as a comprehensive middleware portfolio for collaboration, predictive analytics, software development, and systems administration, as well as the world’s most advanced servers and supercomputers.
Matrix42 UEM
Matrix42 Unified Endpoint Management combines the benefits of Enterprise Mobility Management’s (EMM) Modern Management capabilities with Client Lifecycle Management’s (CLM) Classic Management features in a single solution.
Matrix42 Inventory’s auto-discovery feature ensures complete transparency by automatically providing an up-to-date overview of all hardware and software in use. Virtual machines and hybrid devices, such as those that run Windows 10, are also identified, assigned, and their relationships are documented.
Data Quality Improvement — By combining Matrix42 Inventory with Service and Software Asset Management, you can make important data available in a single database for all processes. It serves as the foundation for streamlining your Service Management operations, as well as lowering your license and IT asset management expenses. Intuitive and simple to use – See what is running on a client in real-time and schedule installation windows when it is most convenient for you. You can assign work to less specialized personnel or even the user with comprehensive authorization management. You may simply control operations in your inventory via the API using PowerShell, Matrix42 Workflow Studio, or custom programming.
Sophos Mobile
Sophos Mobile is a UEM Software solution that enables enterprises to manage and secure traditional and mobile endpoints with less time and effort. Sophos Mobile, the only unified endpoint management solution that integrates natively with a leading next-gen endpoint security platform, manages and secures Windows 10, macOS, Android, and iOS devices in the easy-to-use unified Sophos Central admin interface alongside other Sophos security products. Sophos Mobile is the ideal method to centralize endpoint management for consistent policies, complete security, and enabling people to be productive on the devices they prefer, thanks to industry-leading mobile threat defense (MTD) employing Intercept X for Mobile and best-in-class data protection.
SafeGuard Encryption instantly encrypts content as soon as it is created. When data is shared across the cloud, email, platforms, and devices, encryption is maintained. Before granting access to encrypted data, Synchronized Encryption continually evaluates the user, application, and security integrity of a device. SafeGuard syncs encryption keys with Sophos Mobile’s Secure Workspace app, allowing users to safely view, access, and share encrypted data.
Conclusion
In this article, we have seen UEM Software and various tools that allow businesses to monitor company data, licenses, applications, usage, and security across a wide range of devices from a central location. You can choose any of them based on your requirements. I hope you will find this article helpful.
For more options and information on UEM Software, head to Saasworthy.com.
Also read
Top 8 Email Encryption Software in 2022
Boost Your Email Marketing Success with these 6 Top Email Verification Tools