|
|
90% SW Score The SW Score ranks the products within a particular category on a variety of parameters, to provide a definite ranking system. Read more 
Visit Website
|
80% SW Score The SW Score ranks the products within a particular category on a variety of parameters, to provide a definite ranking system. Read more 
Visit Website
|
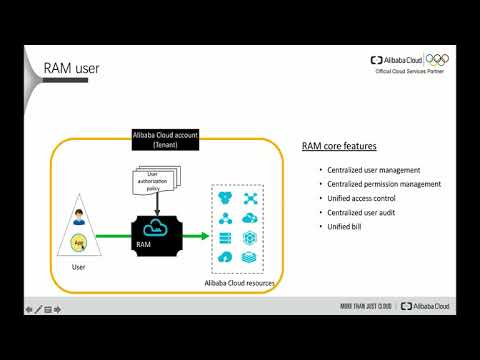
| Description | Idaptive provides Next-Gen Access solutions to enterprises to protect them from unauthorized data access, cyber-attacks, and data breaches. It follows a Zero Trust and Security First approach to regulate access of each of the users by verifying them and validating their devices. The Multi-Factor Authentication creates an additional layer of security before any access is granted to applications. The software can monitor the network, device, and learn user behavior context to assign risk levels to each accessed event. By securely authenticating every access with a wide range of supported factors that also includes FIDO2 keys, virtual and hardware tokens, etc, Idaptive eliminates the need of using passwords. Admins can route application access requests, create application accounts, revoke access whenever necessary, etc easily. Enterprises can frame centralized policy management and secure endpoints that are used to access enterprise resources. With device security management, institutions can also extend enterprise authentication services to the cloud without duplicating identities. One can even select trusted devices to limit access to certain information and applications. If needed, data sets can be locked and deleted within minutes in the case of cyberattacks. Besides, there are several other security features as well that can be implemented to build robust cybersecurity within an organization. Read more | Alibaba Cloud Resource Access Management (RAM) is a user management and access control solution that allows you to centrally manage your users (including personnel, systems, and applications) and securely regulate their access to your resources via permission levels. As a result, RAM enables you to securely provide Alibaba Cloud resource access permissions to only your chosen high-privileged users, enterprise professionals, and partners. This ensures that your cloud resources are used safely and appropriately, as well as preventing unauthorized access to your account. RAM enables you to control access to Alibaba Cloud services and resources from a single location. RAM users and user groups can be created and managed using RAM. You can also give RAM individuals and user groups authorization to limit their access to cloud resources. You can manage different user identities and issue permissions for resource access with Alibaba Cloud Resource and Access Management (RAM). Alibaba Cloud RAM's major function is to assign and manage an access lifecycle for each product deployment for an organization by keeping digital identities. An overview of Alibaba Cloud Resource and Access Management (RAM) will be provided in this post. Read more |
| Pricing Options |
|
|
| SW Score & Breakdown |
90% SW Score The SW Score ranks the products within a particular category on a variety of parameters, to provide a definite ranking system. Read more
|
80% SW Score The SW Score ranks the products within a particular category on a variety of parameters, to provide a definite ranking system. Read more
|
| SaaSworthy Awards | # 4 Highly Rated # 4 Most Popular |
Not Available
|
| Total Features |
11 Features
|
8 Features
|
| Common Features for All |
API Access Management
Access Request Management
Account Management
Compliance Management
Multi-factor Authentication
Password Management
Passwordless Login
Role Management
Single Sign-On (SSO)
Social Sign On
User Activity Monitoring
|
API Access Management
Access Request Management
Account Management
Compliance Management
Multi-factor Authentication
Password Management
Passwordless Login
Role Management
Single Sign-On (SSO)
Social Sign On
User Activity Monitoring
|
| Organization Types Supported |
|
|
| Platforms Supported |
|
|
| Modes of Support |
|
|
| API Support |
|
|
| User Rating |
|
|
| Ratings Distribution |
|
|
| Review Summary |
Reviewers praise Idaptive's user-friendliness, highlighting its intuitive interface and straightforward setup process. They also commend its robust security features, including multi-factor authentication and single sign-on, which enhance overall security posture. Additionally, reviewers appreciate Idaptive's seamless integration with existing IT infrastructure, enabling smooth deployment and centralized management. However, some users have expressed concerns regarding occasional performance issues and limited customization options. |
Not Available
|
| Read All User Reviews | Read All User Reviews |
AI-Generated from the text of User Reviews
| Pricing Options |
|
|
|
Pricing Plans
Monthly Plans
Annual Plans
|
Single Sign-on Others Multi-factor Authentication Others Lifecycle Management Others Mobile Devices Others Endpoint Management Others |
Alibaba Resource Access Management Free |
|
View Detailed Pricing
|
View Detailed Pricing
|





|


Oracle Identity Management
3.8 Based on 99 Ratings Alibaba Resource Access Management Vs Oracle Identity Management
IBM Security Verify Access
3.3 Based on 32 Ratings Alibaba Resource Access Management Vs IBM Security Verify Access
PingAccess
4.6 Based on 25 Ratings |
|
| Videos |

+ 2 More
|
|
| Company Details | Located in: Santa Clara, California Founded in: 2018 | Located in: Hangzhou, China |
| Contact Details |
Not available https://www.idaptive.com/ |
Not available https://www.alibabacloud.com/product/ram |
| Social Media Handles |
|
Not available |

Looking for the right SaaS
We can help you choose the best SaaS for your specific requirements. Our in-house experts will assist you with their hand-picked recommendations.

Want more customers?
Our experts will research about your product and list it on SaaSworthy for FREE.