When it comes to security, it’s always said that prevention is better than cure. Yet, with attacks increasing day by day, it’s difficult to predict the same. Add to it the fact that the ongoing pandemic has made remote work the norm, which increases the attack surface. That’s why a concept called Zero Trust Access has become popular, ensuring that nothing should be trusted by default. While Zero Trust, as a concept, has become popular recently, InstaSafe has been offering the same since its inception in 2012, so it was our pleasure to interact with Mr Sandip Kumar Panda, co-founder and CEO. We talked about his journey, Instasafe’s evolution, its roadmap, and more.
PS: the interview has been edited for the sake of brevity.

Table of Contents
1) Before we begin talking about InstaSafe, can you share your journey into the world of SaaS?
It has been a roller-coaster ride as I moved on from the corporate space to enter the SaaS startup phase, and we evolved to become a leading Cloud-based Security-as-a-Service solution provider delivering comprehensive and uncompromising protection against cyber threats and attacks.
Of course, there are always multiple trials and tribulations when it comes to SaaS businesses. But that is exactly what draws you to the idea of venturing into SaaS; the idea that you can solve problems that would cost billions of dollars, purely based on a software, an otherwise intangible entity.
The traditional Indian enterprise is often reluctant to spend on cybersecurity, and more so on a solution based on an approach that was devised less than a decade back. We had to initially face roadblocks in explaining what our solutions stood for, and more so in how they were much more effective in securing a prospective client’s critical assets, as compared to their existing security setup. While this changed over time, and with the advent of recent cloud security solutions as a viable replacement for legacy-based security systems, we have had to go through a huge learning curve on the road to running a successful startup. Our relations with our customers have always been a ‘give and take’ relationship, and we believe that where our product stands today is a reflection of the efforts of both our development team, as well as our customers. Our solutions relied on a process of continuous innovation and improvement, based on a combination of market factors and customer feedback, and although we are happy with where our products and our company stand today, we hope to never stop innovating. In addition, our highly experienced team and the positive feedback we keep receiving from organizations of all sizes, fuels our passion for solving the ever growing need to protect organizations from security threats and attacks that have been growing at an alarming rate
2) What gaps did you see in the market that led you to launch InstaSafe?
Today, security has become an indispensable necessity for organizations of any size whatsoever. The pace of digital transformation has ensured that security remains relevant. In additions, the evolution of cyber threats into more clever, subtle, and lethal forms has also become a cause of concern. Over time, the discussion on cybersecurity has moved from the IT department to the entire organization.
The major issue that was associated with cybersecurity in the early 2010s was the inherent complexity of the solutions of the day. Too many cooks spoiled the broth, leading to multiple vulnerabilities that could be exploited to exfiltrate critical data. Especially with digital transformation, every asset was potentially suspicious, and the need arose for adaptive solutions that could help in continuously identifying and validating who is to be trusted.
With more and more enterprises migrating their applications to the cloud, companies that were turning digital, had to open up their tightly secured network perimeter to a multitude of users that not only included remote employees, but also third-party partners. In this scenario, security tech of the day proved ineffective. Data, no matter how confidential, had to be accessible from anywhere. A scalable solution that understood the modern network needs and secured the flow of this data was the need of the day.
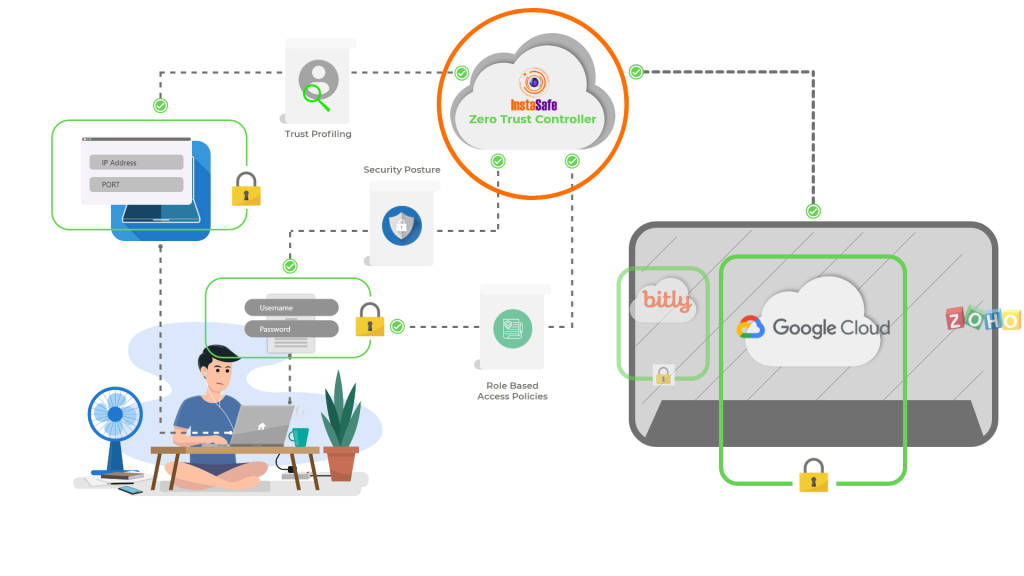
With this in mind, InstaSafe was founded in 2012, with a singular mission of simplifying security, both for security teams and for the end user. We relied on a process of continuously authenticating, authorising, and monitoring every user for every request made to access corporate applications. In effect, we removed the very concept of a network perimeter, and replaced it with micro-perimeters, wherein every user, her device, and the apps she’s allowed to access were divided into small perimeters. By using a Zero Trust Approach, there was no discrimination between resources within the network and the ones outside the network, with all devices being assigned Zero Implicit Trust. Today, Zero Trust has become mainstream, owing to its elasticity, security, and scalability. With more organisations adopting a work from home policy, the viability and practicality of Zero Trust solutions has come into spotlight. InstaSafe has grown at a rapid pace during this transitional period, making it to the coveted list of the fastest growing tech companies of the country. While the way we work has certainly matured, we are still hungry to innovate, and solve every modern security challenge that comes our way.
3) Can you share some use cases for the audience to understand what zero trust access is why it’s important?
In terms of defining use cases and scenarios for a Zero Trust Model, Zero Trust Technologies are touted to form the backbone of security infrastructures in the next decade. Leading market research agencies have predicted that in the next 5 years or so, almost 80 percent of companies will replace their existing VPN systems for Zero Trust Tech. And this is mostly due to the flexibility and hyperscalability associated with Zero Trust Models. Zero Trust not only allows for secure and scalable remote access that can be deployed within days, but also enables a secure cloud migration experience. These 2 use cases become especially important I the present context, when both applications and workforces are moving out of premises. Zero Trust Technologies also provide a unified platform for security of both on premise and cloud assets, without discriminating on the basis of network locality. Among other critical use cases, the concept of segmentation and continuous validation finds use in IoT and BYOD Security, while the DevOps teams also find a way of secure collaboration through Zero Trust.
4) Could you tell us about how InstaSafe has evolved since its launch in 2012?
We are developing our product suite as per modern network needs, but our mission still remains the same. Which is why we are looking to ensure an integrated security experience for our customers through a product suite that looks to complement our Zero Trust Solutions by extending security for applications of all kinds. Over the years, our products have evolved as solutions that break the traditional security myths, and provide an innovative and perfectly engineered solution to stop the next generation of hackers. We started with a solution that relied on a relatively crude concept back them. With time, we have gone on to add integrations, and features that cater to modern security challenges. Features like behavioural biometrics, and adaptive multifactor authentication have gone on to add to the security layers of an enterprise. Similarly, a feature like geo-binding helps in binding users to their devices, and in the process, ensuring greater security.
In the course of our journey, we realized that there remained a certain gap in the way enterprises, small, medium, and large, tested their applications for vulnerabilities. To solve this gap, we decided to tap into the huge pool of hackers across the world, and employ them to identify bugs in enterprise applications, in return for a bounty. That gave birth to SafeHats, India’s first managed bug bounty program, or crowdsourced vulnerability disclosure program, if you will.
Adaptation to current security challenges has helped us in determining how best to solve customer problems. We actively engage in detailed customer feedback sessions, and try to incorporate the solutions to their problems in our product upgrades. As a result, over the period of 8 years, we have seen multiple iterations of our offerings, each a significant step ahead of its predecessor. In retrospect, this does give an advantage.
5) Could you share how many customers do you have now? And what kind of industries are using InstaSafe the most?
We like to think of ourselves as a growth stage startup with an early stage bent of mind. Our aggressive growth trajectory has led us to serve and secure endpoints for more than half a million end consumers belonging to 100+ Fortune 2000 companies, and also led us to being adjudged among Asia’s fastest growing companies.
6) This space has a lot of players, whether established companies or startups, so how does InstaSafe stand out amidst the competition?
While cybersecurity has matured as a competitive space, there are still relatively few players who have tried to do something more innovative in this sector. Giants like Cisco have set forth benchmarks in innovation, that are left for us to chase, but I believe, given that the Zero Trust market has a size of $3.6billion, there’s a lot of space for healthy competition and disruption between the multiple players that occupy the space.
InstaSafe has managed to carve a niche by being one of the very few players which offer what is called a ‘True’ Zero trust offering. Many VPN providers have tried to reposition and repackage the same obsolete offering as a Zero Trust product by masquerading the same with marketing jargons, but that isn’t the case with InstaSafe, which is why we enjoy the advocacy of some of the world’s foremost CISOs. Truth be told, we were little ahead of our times when organizations were on the cusp of their migration from perimeter set up to either hybrid or CSP models. As I had mentioned in my earlier point, our mission was to provide a simple but effective solution that would disrupt the traditional way of application security and protection that already existed in the markets.
Companies using multiple, obsolete technologies to solve multiple challenges complicating the entire security posture of the company, and leaving open the scope for existence of security loopholes. Our core technologies are designed to tackle this very challenge, and we base our solutions, use cases, and technologies towards designing and operation of security infrastructure that is scalable, secure, flexible and affordable. Cybersecurity, as we see it today, is a highly fragmented sector. Without a well organized Information Security Team, enterprises often find themselves at a wit’s end, trying to figure out which technology best suits their organisation. This often results in companies using multiple, obsolete technologies to solve multiple challenges complicating the entire security posture of the company, and leaving open the scope for existence of security loopholes.
Our core technologies are designed to tackle this very challenge, and we base our solutions, use cases, and technologies towards designing and operation of security infrastructure that is scalable, secure, flexible, and affordable. Most, if not all data security startups, tend to assign some level of implicit trust inside the system. By dividing business systems and processes into ‘inside’ and ‘outside’, and assigning a previously entitled amount of trust to internal systems, we create a divide that is not viable in the modern world. This excessive trust often leads to excessive latent risks that manifest themselves later as an exploited cyberattack. InstaSafe on the other hand, believes that trust never was an entitlement. Trust needs to be earned. It needs to be established by authenticating the credentials of the user, while also validating the context, as to why access is being sought. By employing this unique, zero trust methodology in the design of our technologies, we seek to create a final product that can not only accommodate modern disruptions like the cloud, but also creates a stronger security setup within the enterprise.
It would not be wrong to say that we were one of the first few global players in the Zero Trust domain, when we started in 2012. As the Cloud Security Alliance’s definition of an SDP architecture evolved, we found that we were in a unique position, since we had been helping organisations adopt a Zero Trust approach for some time then, and our products had undergone several iterations and corrections, to come up with a much superior offering than what other Zero Trust players had to offer. I would like to believe that this competitive advantage in terms of product superiority still stands, and this, along with our constant attention towards innovating and accommodating customer feedback in our upgrades to make a people centric solution makes us different,
7) Could you shed a light on InstaSafe’s marketing strategy?
Operating from a B2B niche market is often challenging, but we have learnt to go against the tide and register record numbers consistently over the past 5 years. Our GTM relies on a network of partners, in the form of affiliates, managed security service providers, and others. We also leverage technology marketplaces by establishing a presence in some of the world’s most prominent marketplaces, and making a mark there. In terms of a digital strategy, we have very recently embarked on a digital revamp and restructuring program that allows smaller companies to make contactless demos and sales of our product for smaller number of users. This means an easier customer experience in terms of a B2C like purchase, and an easy to setup and deploy process.
8) How has the ongoing pandemic affected InstaSafe – both in terms of businesses and no of users?
The pandemic has massively disrupted the way businesses operate. A lot of organizations, be it large or small, have now adapted to the situation, and are now contemplating to move to, or have already moved to the remote working model, which was earlier prevalent in the Western countries only.
Of course, managing such large remote workforces, many of whom may try to access enterprise networks using unmanaged devices, or even on unsecured public networks, became a huge security challenge. A majority of enterprises which were still using hardware-based traditional solutions faced a sudden need to scale up their remote connectivity capabilities. This became a hurdle in itself, since scaling up these solutions would involve a cumbersome process, which could span months. A solution was required which would not only be deployable in a matter of weeks, or even days, but would also cater to a variety of remote connectivity use cases for employees spread across multiple geographies. InstaSafe lived up to this massive security and logistic challenge, helping these companies to deploy Zero Trust solutions to scale up instantly and eliminate potentially adverse business impacts in many cases.
As we acclimatized with the challenges brought by the lockdowns, a number of our existing customers immediately moved to our solution to empower their employees to work from home securely. We also welcomed a number of new forward-looking businesses, who adopted InstaSafe to help ensure business continuity. We’ve been instrumental in scaling up businesses across verticals, be it IT&ITES, Retail, and Hospitality, etc. who scaled up their businesses from a few hundred users to 1000s globally in a matter of weeks. Our log reports proved to be handy for the HR teams to analyze the productivity of remote employees.
At the same time, we recognised one of the primary challenges that many organisations would face in the light of the outbreak and the impending lockdown it caused. Due to the lockdown, many organisations, especially those belonging to the MSME sector, were found to be inadequate in terms of securing their endpoints and extending remote access to their workforce. With InstaSafe Emergency Access, we provided free installation and support charges for 60 days to these organisations, and rolled out special plans to support them thereafter.
Given that InstaSafe ZTNA / ZTAA solutions are scalable on demand, and doesn’t require significant training to use the interface, we have received an elated response from all our customers.
9) What’s next for InstaSafe? Any new features that you’re working on?
We are looking forward to expanding on the Zero Trust mission, which is why we have started R&D for Mobile Device Management and Authenticator offerings that leverage the Zero trust Model and ensure complete security of devices.
10) What are your favorite SaaS products out there?
We are a tech savvy company and love to dabble around with various SaaS tools to drive growth and streamline processes. I do have a list of favorites when it comes to SaaS tools for growth. Zoho Suite offers a wide range of business, sales, and customer management tools that have a smooth interface. Apollo is a very cost-effective tool to generate contact information and gather some rudimentary form of intent data. Other than that, we do use Gitlab for collaboration between our dev team, and it has proven to be highly efficient in streamlining our processes.






